NKCTF2024还有两周就快开始了,复现一下NKCTF2023
baby_RSA
题目
1 | from Crypto.Util.number import * |
题解:
先是老生常见的dp泄露 ,然后:
$P = m^p \bmod n=m+k_1p$
$Q = m^q \bmod n=m+k_2q$
$P*Q=m^2+m(k_1p+k_2q)+k_1k_2pq$
所以copper里的多项式就出来了:$P*Q=m^2+m(P-m+Q-m) \bmod n$
exp:
1 | import libnum |
解2:
一般是消项凑公因子的思路
$P^{pq} = (m^{pq})^p \bmod n=m \bmod p=m+k_1p$
$Q^{pp} = (m^{pq})^p \bmod n=m \bmod p$ ==> $Q= m \bmod p=m+k_2p$
$P^{pq}-Q=p(k_1-k_2)$
exp:
1 | import libnum |
ez_math
题目
1 | from Crypto.Util.number import getPrime, bytes_to_long |
题解:
$a^{e_1} = 3 \bmod n$
$a^{e_2} = 9 \bmod n$
所以 $a^{2e_1}\equiv a^{e_2} \bmod n$ ==> $a^{2e_1-e_2}=1 \bmod n$
由欧拉定理得,$2e_1-e_2=\varphi(n)$
exp:
1 | import libnum |
ezRSA
题目
1 | from Crypto.Util.number import * |
题解:
第一部分观察细节:知道n和phi,直接可以搜到相关分解n的脚本(已知n和phi,分解n)
第二部分同baby_RSA:
$c_2^{q_1p_1}=m_2 \bmod p_1 $
$c_3=m_2 \bmod p_1$
$c_2^N-c_3=p_1(k_1-k_2)$
1 | import gmpy2 |
real_MT
题目
1 | import random |
题解:
移步MT19937 实战 | W’Blog (wbuildings.github.io)
fake_MT
题目
1 | import random |
题解:
题目源码不说和real_MT长得像,简直是一模一样,一说这题是python2的环境
题解如上,和real_MT一样
同上,移步MT19937 实战 | W’Blog (wbuildings.github.io)
ez_polynomial
题目:
1 | #sage |
题解:
多项式RSA ,先分解一下N,得到 phi
多项式的phi,$\varphi=p^n-1$ ,p为GF(p)的模数,n为此多项式最高项次数
所以这里的phi等于: $\varphi(N)=(p^n-1)*(p^n-1)$
然后常规解再取多项式的系数就行
exp:
1 | #Sage |
这题是原题,脚本参考:
RSA | Lazzaro (lazzzaro.github.io)
eZ_Bl⊕ck
题目:
1 | from Crypto.Util.strxor import strxor as xor |
题解:
1 | print(encode(r, key)) |
这样给了一个例子再给你加密的,要么通过前者求出key,要么两者消掉key,后者居多
八层异或罢了
看不出来就写下来,把每个步骤写下来,不要眼高手低(bushi)
记 r1 = [:16],r2 = [16:],m1 = [:16],m2 = [16:],rc1 = [:16],rc2 = [16:],mc1 = [:16],mc2 = [16:]
第一层
前一半:r1^r2^key1 后一半:r1
第二层
前一半:r2^key1^key2 后一半:r1^r2^key1
第三层
前一半:r1^key2^key3 后一半:r2^key1^key2
第四层
前一半:r1^r2^key1^key3^key4 后一半:r1^key2^key3
第五层
前一半:r2^key1^key2^key4^key5 后一半:r1^r2^key1^key3^key4
第六层
前一半:r1^key2^key3^key5^key6 后一半:r2^key1^key2^key4^key5
第七层
前一半:r1^r2^key1^key3^key4^key6^key7 后一半:r1^key2^key3^key5^key6
第八层
前一半:r2^key1^key2^key4^key5^key7^key8 后一半:r1^r2^key1^key3^key4^key6^key7
看得出来,m1、m2 同理
第八层
前一半:m2^key1^key2^key4^key5^key7^key8 后一半:m1^m2^key1^key3^key4^key6^key7
所以 m2 = mc1^rc1^r2 ,m1 = mc2^rc2^r1^r2^m2
1 | m = flag.strip(b'NKCTF{').strip(b'}').replace(b'-', b'') |
最后拼接转成 uuid 的格式就行了
exp:
1 | import uuid |
easy_high
题目
1 | from Crypto.Util.number import * |
题解:
我早期的一篇博客写的挺详细的,适合初学者,请移步(划到最后):RSA刷题系列(施工中) - Wbuildings - 博客园 (cnblogs.com)
把 m 的长度调到 合理范围内就行了
exp:
1 | import libnum, gmpy2 |
eZ_LargeCG
题目
1 | from gmpy2 import next_prime |
题解:
典型的 Pollard’s p-1、William’s p+1 ,脚本参考: RSA | Lazzaro (lazzzaro.github.io)
最后一步是 矩阵快速幂 ,
1 | (a * A[-3] + b * A[-2] + c * A[-1] + d) % n |
据此构造矩阵
同时 题目说明 p1<q1,p2<q2
exp:
1 | # python |
原题:
RSA中利用光滑数进行模数分解-CSDN博客
complex_matrix
题目
1 | from Crypto.Util.number import * |
题解:
d 为 400bit,N为 741*2 bit,
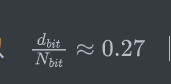
所以,d的大小在Boneh Durfee 攻击范围内
我调的是m=8,求得 d 后就是,已知ed 分解 n
Boneh Durfee 脚本在此 2023年春秋杯网络安全联赛冬季赛 | W’Blog (wbuildings.github.io)
exp:
1 | e = 65128799196671634905309494529154568614228788035735808211836905142007976099865571126946706559109393187772126407982007858423859147772762638898854472065889939549916077695303157760259717113616428849798058080633047516455513870697383339784816006154279428812359241282979297285283850338964993773227397528608557211742425548651971558377656644211835094019462699301650412862894391885325969143805924684662849869947172175608502179438901337558870349697233790535 |
还可以拓展维纳攻击?
拓展维纳攻击:给了多个指数 $e_i$
Dexterjie师傅测试了3,4,5,6个e,都能够跑出结果,不过跑6个e的需要挺长时间
Xenny给出测试结论:大约8个e 的情况已经运行不出来了
(我才知道这个wiki博客是Xenny师傅的博客,恐怖如斯😭😭)
扩展维纳攻击 - CTF Wiki (ctf-wiki.org)
这边存一下 拓展维纳攻击 的脚本:
1 | import gmpy2 |
baby_classical(未明白)
题目
1 | import string |
题解:
1 | def decrypt(self, ciphertext: np.ndarray) -> str: |
放弃了,看不懂,存个脚本(我的GPT怎么就写不出来啊)
NKCTF2023·Crypto WP | Harry’s Blog (harry0597.com)
exp:
1 | import string |
Raven
题目
1 | #!/usr/bin/env sage |
题解:
Shamir门限秘密共享方案, SSS,见:
(^▽^)我藏好了哦~Shamir门限方案 | W’Blog (wbuildings.github.io)
1 |
PsychoRandom
题目
task.py
1 | #!/usr/bin/env python |
utils.py
1 | class ToyGen: |
题解
Reference:
NKCTF2023·Crypto WP | Harry’s Blog (harry0597.com)
NKCTF | DexterJie’Blog